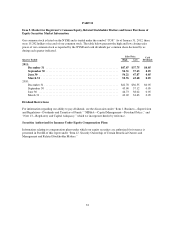
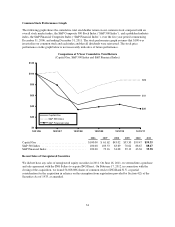
Capital One 2011 Annual Report Download - page 45
Download and view the complete annual report
Please find page 45 of the 2011 Capital One annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.In addition, our on-going investments in infrastructure, which may be necessary to maintain a competitive
business, integrate newly acquired businesses such as ING Direct and HSBC’s U.S. credit card business and
establish scalable operations, may increase our expenses. Further, as our business develops, changes or expands,
additional expenses can arise as a result of a reevaluation of business strategies, management of outsourced
services, asset purchases or other acquisitions, structural reorganization, compliance with new laws or regulations
or the integration of newly acquired businesses. If we are unable to successfully manage our expenses, our
financial results will be negatively affected.
We Could Incur Increased Costs or Reductions In Revenue Or Suffer Reputational Damage In the Event Of
The Theft, Loss or Misuse Of Information, Including As A Result Of A Cyber-Attack.
Our products and services involve the gathering, storage and transmission of sensitive information regarding our
customers and their accounts. Our ability to provide such products and services, many of which are web-based,
relies upon the management and safeguarding of information, software, methodologies and business secrets. To
provide these products and services, we use information systems and infrastructure that we and third party
service providers operate. We also have arrangements in place with retail partners and other third parties where
we share and receive information about their customers who are or may become our customers. As a financial
institution, we also are subject to and examined for compliance with an array of data protection laws, regulations
and guidance, as well as to our own internal privacy and information security policies and programs. If
unauthorized persons were somehow to get access to personal, confidential or proprietary information, including
customer information, in our possession or to our proprietary information, software, methodologies and business
secrets, it could result in significant legal and financial exposure, supervisory liability, damage to our reputation
or a loss of confidence in the security of our systems, products and services that could adversely affect our
business.
Information security risks for large financial institutions like us have generally increased in recent years in part
because of the proliferation of new technologies, the use of the Internet and telecommunications technologies to
conduct financial transactions and the increased sophistication and activities of organized crime, perpetrators of
fraud, hackers, terrorists, activists and other external parties. As noted above, our operations rely on the secure
processing, transmission and storage of confidential information in our computer systems and networks. Our
businesses rely on our digital technologies, computer and email systems, software and networks to conduct their
operations. In addition, to access our products and services, our customers may use computers, personal
smartphones, tablet PC’s and other mobile devices that are beyond our security control systems. Although we
believe we have a robust suite of authentication and layered information security controls, our technologies,
systems, networks and our customers’ devices may become the target of cyber-attacks or other attacks that could
result in the unauthorized release, gathering, monitoring, misuse, loss or destruction of our or our customers’
confidential, proprietary or other information, including their access credential to accounts with online
functionality, or that could result in disruptions to the business operations of us or our customers or other third
parties. Further, a breach or attack affecting one of our third-party service providers or partners could impact us
through no fault of our own.
Because the methods and techniques employed by perpetrators of fraud and others to attack, disable, degrade or
sabotage platforms, systems and applications change frequently and often are not fully recognized or understood
until after they have been launched, we and our third-party service providers and partners may be unable to
anticipate certain attack methods in order to implement effective preventative measures. Should a cyber-attack
against us succeed on any material scale, market perception of the effectiveness of our security measures could
be harmed, and we could face the aforementioned risks. Though we have insurance against some cyber-risks and
attacks, it may not be sufficient to offset the impact of a material loss event.
The Growth Of Our Online Banking Business Presents Certain Risks.
As a result of our strategic decisions and recent acquisitions, including ING Direct, we have grown our online
banking business significantly over the past few years. Today, we operate one of the largest online banking
25