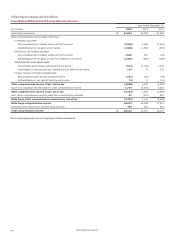
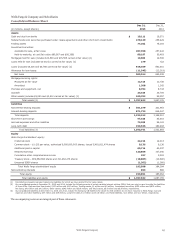
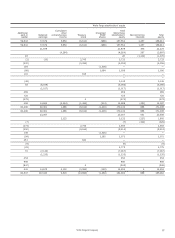
Wells Fargo 2015 Annual Report Download - page 129
Download and view the complete annual report
Please find page 129 of the 2015 Wells Fargo annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.respect to an insured loan, we might incur higher credit losses if
replacement coverage is not obtained. For example, in October
2011, PMI Mortgage Insurance Co. (PMI) was seized by its
regulator. Although only a limited amount of loans and
securities held in our portfolios had PMI insurance support, we
cannot be certain that any future financial difficulties or credit
downgrades involving one of our mortgage insurance company
providers will not materially adversely affect our mortgage
business and/or financial results. We also have investments in
municipal bonds that are guaranteed against loss by bond
insurers. The value of these bonds and the payment of principal
and interest on them may be negatively affected by financial
difficulties or credit downgrades experienced by the bond
insurers.
For more information, refer to the “Balance Sheet Analysis
– Investment Securities” and “Risk Management – Credit Risk
Management– Liability for Mortgage Loan Repurchase Losses”
sections in this Report.
OPERATIONAL AND LEGAL RISK
A failure in or breach of our operational or security
systems or infrastructure, or those of our third party
vendors and other service providers, including as a
result of cyber attacks, could disrupt our businesses,
result in the disclosure or misuse of confidential or
proprietary information, damage our reputation,
increase our costs and cause losses. As a large financial
institution that serves over 70 million customers through 8,700
locations, 13,000 ATMs, the Internet, mobile banking and other
distribution channels across the U.S. and internationally, we
depend on our ability to process, record and monitor a large
number of customer transactions on a continuous basis. As our
customer base and locations have expanded throughout the U.S.
and internationally, and as customer, public, legislative and
regulatory expectations regarding operational and information
security have increased, our operational systems and
infrastructure must continue to be safeguarded and monitored
for potential failures, disruptions and breakdowns. Our business,
financial, accounting, data processing systems or other operating
systems and facilities may stop operating properly or become
disabled or damaged as a result of a number of factors including
events that are wholly or partially beyond our control. For
example, there could be sudden increases in customer
transaction volume; electrical or telecommunications outages;
degradation or loss of public internet domain; climate change
related impacts and natural disasters such as earthquakes,
tornados, and hurricanes; disease pandemics; events arising
from local or larger scale political or social matters, including
terrorist acts; and, as described below, cyber attacks. Although
we have business continuity plans and other safeguards in place,
our business operations may be adversely affected by significant
and widespread disruption to our physical infrastructure or
operating systems that support our businesses and customers.
Information security risks for large financial institutions
such as Wells Fargo have generally increased in recent years in
part because of the proliferation of new technologies, the use of
the Internet and telecommunications technologies to conduct
financial transactions, and the increased sophistication and
activities of organized crime, hackers, terrorists, activists, and
other external parties, including foreign state-sponsored parties.
Those parties also may attempt to fraudulently induce
employees, customers, or other users of our systems to disclose
confidential information in order to gain access to our data or
that of our customers. As noted above, our operations rely on the
secure processing, transmission and storage of confidential
information in our computer systems and networks. Our
banking, brokerage, investment advisory, and capital markets
businesses rely on our digital technologies, computer and email
systems, software, and networks to conduct their operations. In
addition, to access our products and services, our customers may
use personal smartphones, tablet PC’s, and other mobile devices
that are beyond our control systems. Although we believe we
have robust information security procedures and controls, our
technologies, systems, networks, and our customers’ devices may
become the target of cyber attacks or information security
breaches that could result in the unauthorized release, gathering,
monitoring, misuse, loss or destruction of Wells Fargo’s or our
customers’ confidential, proprietary and other information, or
otherwise disrupt Wells Fargo’s or its customers’ or other third
parties’ business operations. For example, various retailers have
reported they were victims of cyber attacks in which large
amounts of their customers’ data, including debit and credit card
information, was obtained. In these situations we generally incur
costs to replace compromised cards and address fraudulent
transaction activity affecting our customers.
Third parties with which we do business or that facilitate
our business activities, including exchanges, clearing houses,
financial intermediaries or vendors that provide services or
security solutions for our operations, could also be sources of
operational and information security risk to us, including from
breakdowns or failures of their own systems or capacity
constraints.
To date we have not experienced any material losses relating
to cyber attacks or other information security breaches, but there
can be no assurance that we will not suffer such losses in the
future. Our risk and exposure to these matters remains
heightened because of, among other things, the evolving nature
of these threats, the prominent size and scale of Wells Fargo and
its role in the financial services industry, our plans to continue to
implement our Internet banking and mobile banking channel
strategies and develop additional remote connectivity solutions
to serve our customers when and how they want to be served,
our expanded geographic footprint and international presence,
the outsourcing of some of our business operations, and the
current global economic and political environment. For example,
Wells Fargo and other financial institutions continue to be the
target of various evolving and adaptive cyber attacks, including
malware and denial-of-service, as part of an effort to disrupt the
operations of financial institutions, potentially test their
cybersecurity capabilities, or obtain confidential, proprietary or
other information. As a result, cybersecurity and the continued
development and enhancement of our controls, processes and
systems designed to protect our networks, computers, software
and data from attack, damage or unauthorized access remain a
priority for Wells Fargo. We are also proactively involved in
industry cybersecurity efforts and working with other parties,
including our third-party service providers and governmental
agencies, to continue to enhance defenses and improve resiliency
to cybersecurity threats. As cyber threats continue to evolve, we
may be required to expend significant additional resources to
continue to modify or enhance our protective measures or to
investigate and remediate any information security
vulnerabilities.
Disruptions or failures in the physical infrastructure or
operating systems that support our businesses and customers, or
cyber attacks or security breaches of the networks, systems or
devices that our customers use to access our products and
services could result in customer attrition, financial losses, the
inability of our customers to transact business with us, violations
Wells Fargo & Company
127