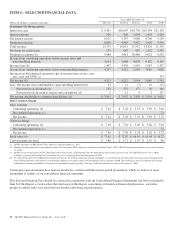
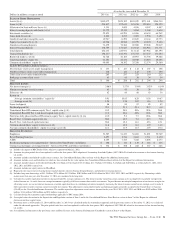
PNC Bank 2014 Annual Report Download - page 40
Download and view the complete annual report
Please find page 40 of the 2014 PNC Bank annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.holders of our cards who have made purchases from that
business may experience fraud on their card accounts. PNC
may suffer losses associated with reimbursing our customers
for such fraudulent transactions on customers’ card accounts,
as well as for other costs related to data security compromise
events, such as replacing cards associated with compromised
card accounts. In addition, PNC provides card transaction
processing services to some merchant customers under
agreements we have with payment networks such as Visa and
MasterCard. Under these agreements, we may be responsible
for certain losses and penalties if one of our merchant
customers suffers a data security breach.
Over the last several years, several large retailers, prominently
including Target and Home Depot, disclosed that they had
suffered substantial data security breaches compromising
millions of card accounts. To date, PNC’s losses and costs
related to these breaches have not been material, but other
similar events in the future could be more significant to PNC.
There have been other recent publicly announced cyber
attacks that were not focused on gaining access to credit card
information but instead sought access to a range of other types
of confidential information including internal emails and other
forms of customer financial information or sought to capture
and possibly shutdown systems and devices maintained by
target companies. Notable examples include attacks in 2014
on JP Morgan Chase and Sony Pictures and in early 2015 on
Anthem. These other attacks have generally not had any
financial impact on PNC but demonstrate the risks to
confidential information and systems operations potentially
posed by cyber attacks.
Methods used by others to attack information systems change
frequently (with generally increasing sophistication), often are
not recognized until launched against a target, may be
supported by foreign governments or other well-financed
entities, and may originate from less regulated and remote
areas around the world. As a result, we may be unable to
address these methods in advance of attacks, including by
implementing adequate preventive measures.
We have policies, procedures and systems (including business
continuity programs) designed to prevent or limit the effect of
possible failures, interruptions or breaches in security of
information systems. We design our business continuity and
other information and technology risk management programs
to manage our capabilities to provide services in the case of an
event resulting in material disruptions of business activities
affecting our employees, facilities, technology or suppliers.
We regularly seek to test the effectiveness of and enhance
these policies, procedures and systems.
Our ability to mitigate the adverse consequences of such
occurrences is in part dependent on the quality of our business
continuity planning and our ability to anticipate the timing and
nature of any such event that occurs. The adverse impact of
natural and other disasters, terrorist activities, international
hostilities and the like could be increased to the extent that
there is a lack of preparedness on the part of national or
regional governments, including emergency responders, or on
the part of other organizations and businesses with which we
deal, particularly those on which we depend but have no
control over.
In recent years, we have incurred significant expense towards
improving the reliability of our systems and their security
against external and internal threats. Nonetheless, there
remains the risk that an adverse event might occur. If one does
occur, we might not be able to remediate the event or its
consequences timely or adequately. To the extent that the risk
relates to products or services provided by others, we seek to
engage in due diligence and monitoring to limit the risk, but
here as well we cannot eliminate it. Should an adverse event
affecting another company’s systems occur, we may not have
indemnification or other protection from the other company
sufficient to compensate us or otherwise protect us from the
consequences.
The occurrence of any failure, interruption or security breach
of any of our information or communications systems, or the
systems of other companies on which we rely, could result in
a wide variety of adverse consequences to PNC. This risk is
greater if the issue is widespread or results in financial losses
to our customers. Possible adverse consequences include
damage to our reputation or a loss of customer business. We
also could face litigation or additional regulatory scrutiny.
Litigation or regulatory actions in turn could lead to liability
or other sanctions, including fines and penalties or
reimbursement of customers adversely affected by a systems
problem or security breach. Even if we do not suffer any
material adverse consequences as a result of events affecting
us directly, successful attacks or systems failures at other
financial institutions could lead to a general loss of customer
confidence in financial institutions, including PNC. Also,
systems problems, including those resulting from third party
attacks, whether at PNC or at our competitors, would likely
increase regulatory and customer concerns regarding the
functioning, safety and security of such systems generally. In
that case, we would expect to incur even higher levels of costs
with respect to prevention and mitigation of these risks.
We continually encounter technological change and we
could falter in our ability to remain competitive in this
arena.
The financial services industry is continually undergoing rapid
technological change with frequent introductions of new
technology-driven products and services. The effective use of
technology increases efficiency and enables financial
institutions to better serve customers and to reduce costs. We
have been investing in technology and connectivity to
automate functions previously performed manually, to
facilitate the ability of customers to engage in financial
22 The PNC Financial Services Group, Inc. – Form 10-K