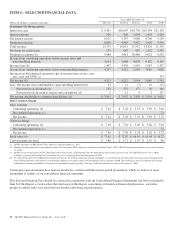
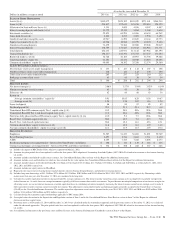
PNC Bank 2014 Annual Report Download - page 39
Download and view the complete annual report
Please find page 39 of the 2014 PNC Bank annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.banking agencies have been taking into account expectations
regarding the ability of banks to meet these new requirements,
including under stressed conditions, in approving actions that
represent uses of capital, such as dividend increases, share
repurchases and acquisitions. Moreover, PNC, as a BHC that
is subject to the advanced approaches for regulatory capital
purposes, is subject to a higher LCR requirement than other
BHCs that have more than $50 billion in total assets but are
not subject to the advanced approaches. Until the scope and
terms of pending or future rulemakings relating to capital,
liquidity, or liability composition are known, the extent to
which such rules may apply to PNC and the potential impact
of such rules on PNC will remain uncertain.
We depend on information systems, both internally and
through third-parties, to conduct our business and could
suffer a material adverse impact from interruptions in the
effective operation of, or security breaches affecting, those
systems.
As a large financial company, we handle a substantial volume
of customer and other financial transactions virtually on a
continuous basis. As a result, we rely heavily on information
systems to conduct our business and to process, record, and
monitor our transactions. In recent years, PNC has increased
substantially in size, scope and complexity. We have also seen
more customer usage of technological solutions for financial
needs and higher expectations of customers and regulators
regarding effective and safe systems operation. We expect
these trends to continue for the foreseeable future. The need to
ensure proper functioning of these systems has become more
challenging, and the costs involved in that effort are greater
than ever.
The risks to these systems result from a variety of factors,
both internal and external. In some cases, these factors are
largely outside of our control, including the potential for bad
acts on the part of hackers, criminals, employees and others.
In other cases, our systems could fail to operate as needed due
to factors such as design or performance issues, human error,
unexpected transaction volumes, or inadequate measures to
protect against unauthorized access or transmissions. We are
also at risk for the impact of natural or other disasters,
terrorism, international hostilities and the like on our systems
or for the effect of outages or other failures involving power
or communications systems operated by others. In addition,
we face a variety of types of cyber attacks, some of which are
discussed in more detail below. Cyber attacks often include
efforts to disrupt our ability to provide services or to gain
access to confidential company and customer information.
We rely on other companies for the provision of a broad range
of products and services. Many of these products and services
include information systems themselves or involve the use of
such systems in connection with providing the products or
services. In some cases, these other companies provide the
infrastructure that supports electronic communications. These
other companies are generally subject to many of the same
risks we face with respect to our systems. To the extent we
rely on these other companies, we could be adversely affected
if they are impacted by system failures, cyber attacks or
employee misconduct.
All of these types of events, whether resulting from cyber
attacks or other internal or external sources, expose customer
and other confidential information to security risks. They also
could disrupt our ability to use our accounting, deposit, loan
and other systems and could cause errors in transactions with
customers, vendors or other counterparties.
In addition, our customers often use their own devices, such as
computers, smartphones and tablets, to do business with us.
We have limited ability to assure the safety and security of our
customers’ transactions with us to the extent they are utilizing
their own devices.
We are faced with ongoing efforts by others to breach data
security at financial institutions or with respect to financial
transactions. Some of these involve efforts to enter our
systems directly by going through or around our security
protections. Others involve the use of schemes such as
“phishing” to gain access to identifying customer information,
often from customers themselves. Most corporate and
commercial transactions are now handled electronically, and
our retail customers increasingly use online access and mobile
devices to bank with us. The ability to conduct business with
us in this manner depends on the transmission of confidential
information, which increases the risk of data security
breaches.
Starting in late 2012, there have been several well-publicized
series of apparently related denial of service attacks on large
financial services companies, including PNC. In a denial of
service attack, individuals or organizations flood commercial
websites with extraordinarily high volumes of traffic, with the
goal of disrupting the ability of commercial enterprises to
process transactions and possibly making their websites
unavailable to customers for extended periods of time. The
attacks against PNC have resulted in temporary disruptions in
customers’ ability to access the corporate website and to
perform on-line banking transactions. To date, no customer
data has been lost or compromised as a result of these attacks
and these efforts have not had a material impact on PNC. We
cannot, however, provide assurance that future attacks of this
type might not have a greater effect on PNC.
As our customers regularly use PNC-issued credit and debit
cards to pay for transactions with retailers and other
businesses, there is the risk of data security breaches at those
other businesses covering PNC account information. When
our customers use PNC-issued cards to make purchases from
those businesses, card account information may be provided to
the business. If the business’s systems that process or store
card account information are subject to a data security breach,
The PNC Financial Services Group, Inc. – Form 10-K 21