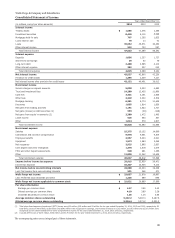
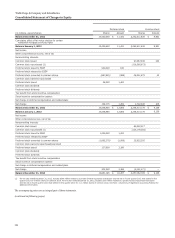
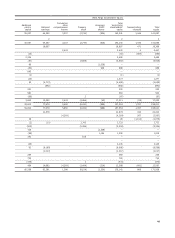
Wells Fargo 2014 Annual Report Download - page 127
Download and view the complete annual report
Please find page 127 of the 2014 Wells Fargo annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.addition, to access our products and services, our customers may
use personal smartphones, tablet PC’s, and other mobile devices
that are beyond our control systems. Although we believe we
have robust information security procedures and controls, our
technologies, systems, networks, and our customers’ devices may
become the target of cyber attacks or information security
breaches that could result in the unauthorized release, gathering,
monitoring, misuse, loss or destruction of Wells Fargo’s or our
customers’ confidential, proprietary and other information, or
otherwise disrupt Wells Fargo’s or its customers’ or other third
parties’ business operations. For example, various retailers have
reported they were victims of cyber attacks in which large
amounts of their customers’ data, including debit and credit card
information, was obtained. In these situations we generally incur
costs to replace compromised cards and address fraudulent
transaction activity affecting our customers.
Third parties with which we do business or that facilitate
our business activities, including exchanges, clearing houses,
financial intermediaries or vendors that provide services or
security solutions for our operations, could also be sources of
operational and information security risk to us, including from
breakdowns or failures of their own systems or capacity
constraints.
To date we have not experienced any material losses relating
to cyber attacks or other information security breaches, but there
can be no assurance that we will not suffer such losses in the
future. Our risk and exposure to these matters remains
heightened because of, among other things, the evolving nature
of these threats, the prominent size and scale of Wells Fargo and
its role in the financial services industry, our plans to continue to
implement our Internet banking and mobile banking channel
strategies and develop additional remote connectivity solutions
to serve our customers when and how they want to be served,
our expanded geographic footprint and international presence,
the outsourcing of some of our business operations, and the
current global economic and political environment. For example,
Wells Fargo and other financial institutions continue to be the
target of various evolving and adaptive cyber attacks, including
malware and denial-of-service, as part of an effort to disrupt the
operations of financial institutions, potentially test their
cybersecurity capabilities, or obtain confidential, proprietary or
other information. As a result, cybersecurity and the continued
development and enhancement of our controls, processes and
systems designed to protect our networks, computers, software
and data from attack, damage or unauthorized access remain a
priority for Wells Fargo. We are also proactively involved in
industry cybersecurity efforts and working with other parties,
including our third-party service providers and governmental
agencies, to continue to enhance defenses and improve resiliency
to cybersecurity threats. As cyber threats continue to evolve, we
may be required to expend significant additional resources to
continue to modify or enhance our protective measures or to
investigate and remediate any information security
vulnerabilities.
Disruptions or failures in the physical infrastructure or
operating systems that support our businesses and customers, or
cyber attacks or security breaches of the networks, systems or
devices that our customers use to access our products and
services could result in customer attrition, financial losses, the
inability of our customers to transact business with us, violations
of applicable privacy and other laws, regulatory fines, penalties
or intervention, reputational damage, reimbursement or other
compensation costs, and/or additional compliance costs, any of
which could materially adversely affect our results of operations
or financial condition.
Our framework for managing risks may not be effective
in mitigating risk and loss to us. Our risk management
framework seeks to mitigate risk and loss to us. We have
established processes and procedures intended to identify,
measure, monitor, report and analyze the types of risk to which
we are subject, including liquidity risk, credit risk, market risk,
interest rate risk, operational risk, legal and compliance risk, and
reputational risk, among others. However, as with any risk
management framework, there are inherent limitations to our
risk management strategies as there may exist, or develop in the
future, risks that we have not appropriately anticipated or
identified. In certain instances, we rely on models to measure,
monitor and predict risks, such as market and interest rate risks,
however there is no assurance that these models will
appropriately capture all relevant risks or accurately predict
future events or exposures. In addition, we rely on data to
aggregate and assess our various risk exposures and any issues
with the quality or effectiveness of our data aggregation and
validation procedures could result in ineffective risk
management practices or inaccurate risk reporting. The recent
financial and credit crisis and resulting regulatory reform
highlighted both the importance and some of the limitations of
managing unanticipated risks, and our regulators remain
focused on ensuring that financial institutions build and
maintain robust risk management policies. If our risk
management framework proves ineffective, we could suffer
unexpected losses which could materially adversely affect our
results of operations or financial condition.
We may incur fines, penalties and other negative
consequences from regulatory violations, possibly even
inadvertent or unintentional violations. We maintain
systems and procedures designed to ensure that we comply with
applicable laws and regulations. However, some legal/regulatory
frameworks provide for the imposition of fines or penalties for
noncompliance even though the noncompliance was inadvertent
or unintentional and even though there was in place at the time
systems and procedures designed to ensure compliance. For
example, we are subject to regulations issued by the Office of
Foreign Assets Control (OFAC) that prohibit financial
institutions from participating in the transfer of property
belonging to the governments of certain foreign countries and
designated nationals of those countries. OFAC may impose
penalties for inadvertent or unintentional violations even if
reasonable processes are in place to prevent the violations. There
may be other negative consequences resulting from a finding of
noncompliance, including restrictions on certain activities. Such
a finding may also damage our reputation as described below
and could restrict the ability of institutional investment
managers to invest in our securities.
Under the Iran Threat Reduction and Syria Human Rights
Act of 2012, we are required to make certain disclosures in our
periodic reports filed with the SEC relating to certain activities
that we or our worldwide affiliates knowingly engaged in
involving Iran during the quarterly period covered by the report.
If we or an affiliate were to engage in a reportable transaction,
we must also file a separate notice regarding the activity with the
SEC, which the SEC will make publicly available on its website.
The SEC will be required to forward the report to the President,
the Senate Committees on Foreign Relations and Banking,
Housing and Urban Affairs, and the House of Representatives
Committees on Foreign Affairs and Financial Services. The
President will then be required to initiate an investigation into
the reported activity and within 180 days make a determination
as to whether to impose sanctions on us. The scope of the
125