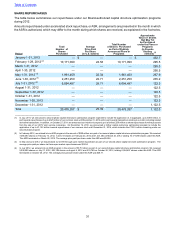
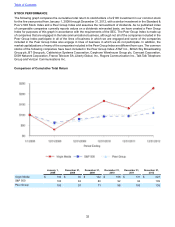
Virgin Media 2012 Annual Report Download - page 23
Download and view the complete annual report
Please find page 23 of the 2012 Virgin Media annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
22
A failure in our network and information systems, whether caused by a natural failure or a security breach,
could significantly disturb our operations, which could have a material adverse effect on those operations,
our business, our results of operations and financial condition.
Certain network and information systems are critical to our business activities. Network and information systems may
be affected by cyber security incidents that can result from deliberate attacks or system failures. These may include,
but are not limited to computer hackings, computer viruses, worms or other destructive or disruptive software, or other
malicious activities. Our network and information systems may also be the subject of power outages, fire, natural
disasters, terrorist attacks, war or other similar events. Theft of metals is particularly acute in the U.K. due to high
prices for scrap metal, and our network is not immune to such thefts. Such events could result in a degradation of, or
disruption to, our cable and non-cable services, and could prevent us from billing and collecting revenue due to us or
could damage our equipment and data or could result in damage to our reputation. Disruption to services could result
in excessive call volumes to call centers that may not be able to cope with such volume, which could in turn have an
adverse effect on our reputation and brand. Our plans for recovery from, and resilience to, such challenges may not
be sufficient. The amount and scope of insurance we maintain against losses resulting from these events may not be
sufficient to cover our losses or otherwise adequately compensate us for any disruptions to our business that may
result.
Sustained or repeated failures of our own or third-party systems that interrupt our ability to provide services to our
customers, prevent us from billing and collecting revenue, or that otherwise prevent us from meeting our obligations
in a timely manner, would adversely affect our reputation and result in a loss of customers and revenue. These network
and information systems-related events could also require significant expenditures to repair or replace damaged
networks or information systems or to protect them from similar events in the future. Further, any security breaches,
such as misappropriation, misuse, penetration by viruses, worms or other destructive or disruptive software, leakage,
falsification or accidental release or loss of information maintained in our information technology systems and networks
or those of our business partners (including customer, personnel and vendor data) could damage our reputation, result
in legal and/or regulatory action against us, and require us to expend significant capital and other resources to remedy
any such security breach. As a result of the increasing awareness concerning the importance of safeguarding personal
information, the potential misuse of such information and legislation that has been adopted or is being considered
regarding the protection, privacy and security of personal information, the liability associated with information-related
risks is increasing, particularly for businesses like ours that handle a large amount of personal customer data. The
occurrence of any such network or information system-related events or security breaches could have a material
adverse effect on our business and results of operations.
Unauthorized access to our network resulting in piracy could result in a loss of revenue.
We rely on the integrity of our technology to ensure that our services are provided only to identifiable paying customers.
Increasingly sophisticated means of illicit piracy of television, broadband and telephony services are continually being
developed in response to evolving technologies. Furthermore, billing and revenue generation for our pay television
services rely on the proper functioning of our encryption systems. While we continue to invest in measures to manage
unauthorized access to our networks, any such unauthorized access to our cable television service could result in a
loss of revenue, and any failure to respond to security breaches could raise concerns under our agreements with
content providers, all of which could have a material adverse effect on our business and results of operations.
We rely on third-party suppliers and contractors to provide necessary hardware, software or operational
support and are reliant on them in a way that could economically disadvantage us.
We rely on third-party vendors to supply us with a significant amount of customer equipment, hardware, software and
operational support necessary to operate our network and systems and provide our services. In many cases, we have
made substantial investments in the equipment or software of a particular supplier, making it difficult for us in the short
term to change supply and maintenance relationships in the event that our initial supplier is unwilling or unable to offer
us competitive prices or to provide the equipment, software or support that we require. In addition, certain provisions
of the Dodd-Frank Wall Street Reform and Consumer Protection Act may soon require us to report on “conflict materials”
used in our products and the due diligence plan we put in place to track whether such minerals originate from the
Democratic Republic of Congo and adjoining countries. The implementation of these requirements could affect the
sourcing and availability of minerals used in certain of our products.
We also rely upon a number of third-party contractors to construct and maintain our network and to install our equipment
in customers' homes. Quality issues or installation or service delays relating to these contractors could result in liability,
reputational harm or contribute to customer dissatisfaction, which could result in additional churn or discourage potential
new customers.
Table of Contents