Experian 2016 Annual Report Download - page 17
Download and view the complete annual report
Please find page 17 of the 2016 Experian annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
15
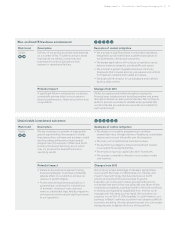
Loss or inappropriate use of data and systems 1 4 6 V
Risk trend Description Examples of control mitigation
Increasing We hold and manage sensitive consumer
information that increases our exposure and
susceptibility to cyber-attacks, either directly
through our online systems or indirectly through
our partners or third-party contractors.
• We deploy physical and technological security
measures, combined with monitoring and alerting
for suspicious activities.
• We maintain an information security programme
for identifying, protecting against, detecting, and
responding to cyber security risks and recovering
from cyber security incidents.
• We impose contractual security requirements on our
partners and other third parties who use our data,
complemented by periodic reviews of third-party controls.
• We maintain insurance coverage, where feasible
and appropriate.
Potential impact Changes from 2015
Losing or misusing sensitive consumer data
could create adverse effects for consumers and
result in material loss of business, substantial
legal liability, regulatory enforcement actions
and/or significant harm to our reputation.
Information security continues to be an increasing risk,
reflecting the growing intensity of threats companies are
facing from cyber-attacks, both domestic and foreign.
We continue to invest in new tools and people, to give us
increased visibility into technical systems, with a keen focus
on identifying suspicious activities. In addition, several
initiatives are underway to complete the standardisation and
centralisation of security management activities. In 2015,
we hired a new Chief Information Officer and a new Chief
Information Security Officer.
In September 2015, we detected unauthorised access to a
server that contained personal identifying information for
consumers who applied for certain services with one of our
clients, T-Mobile USA. No other clients were affected and
our US consumer credit database was not accessed in this
incident. We took immediate action to secure the server and
notified all affected consumers with guidance on how to
protect themselves.
Key
Our strategy:
1 – Consumers at the heart of
what we do
2 – A culture of winning together
3 – Disciplined capital allocation
4 – A powerful brand
5 – Leading, innovative products
6 – Great client outcomes
V – Considered as part of
the viability assessment
Strategic report •Principal risks – identifying and managing risk