IBM 2014 Annual Report Download - page 74
Download and view the complete annual report
Please find page 74 of the 2014 IBM annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
73
Management Discussion
International Business Machines Corporation and Subsidiary Companies
As a globally integrated enterprise, the company operates in
more than 175 countries and is continuing to shift its business to
the higher value segments of enterprise IT. The decrease in total
resources from 2013 to 2014 was primarily due to divestitures in
2014, which drove a reduction of approximately 35,000 resources.
The company continues to remix its skills and resource needs to
match the best opportunities in the marketplace.
The complementary workforce is an approximation of equiv-
alent full-time employees hired under temporary, part-time and
limited- term employment arrangements to meet specific business
needs in a flexible and cost-effective manner.
GLOBAL FINANCING
Global Financing is a reportable segment that is measured as a
stand-alone entity.
In 2014, the Global Financing business remained focused on
its core competencies—providing IT financing to the company’s
clients and business partners. For the year, Global Financing deliv-
ered external revenue of $2,034 million and total revenue of $4,522
million, and expanded gross margin. Total pre-tax income of $2,189
million increased 0.8percent compared to 2013 and return on
equity was 36.8percent.
In addition to the overall health of the economy and its impact
on corporate IT budgets, key drivers of Global Financing’s results
are interest rates and originations. Interest rates directly impact
Global Financing’s business by increasing or decreasing both
financing revenue and the associated borrowing costs. Origi-
nations, which determine the asset base of Global Financing’s
annuity-like business, are impacted by IBM’s non-Global Financing
sales and services volumes and Global Financing’s participation
rates. Participation rates are the propensity of IBM’s clients to
finance their transactions through Global Financing in lieu of paying
IBM up-front cash or financing through a third party.
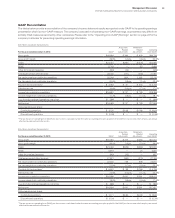
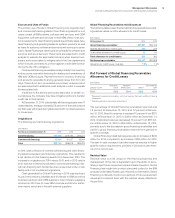
Results of Operations
($ in millions)
For the year ended December 31: 2014 2013 2012
External revenue $2,034 $2,022 $2,013
Internal revenue 2,488 2,282 2,060
Total revenue 4,522 4,304 4,073
Cost 1,428 1,417 1,400
Gross profit $3,094 $2,888 $2,673
Gross profit margin 68.4% 67.1%65.6%
Pre-tax income $2,189 $2,171 $2,034
After-tax income* $1,462 $1,456 $1,362
Return on equity* 36.8% 40.6%41.0%
* See page 77 for the details of the after-tax income and return on equity calculation.
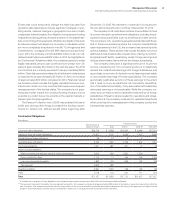
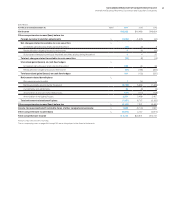
Employees and Related Workforce
Yr.-to-Yr. Percent Change
For the year ended December 31: 2014 2013 2012 2014–13 2013–12
IBM/wholly owned subsidiaries 379,592* 431,212 434,246 (12.0)% (0.7)%
Less-than-wholly owned subsidiaries 8,862 9,018 8,009 (1.7) 12.6
Complementary 24,321 23,555 24,740 3.3 (4.8)
* Reflects reduction of approximately 35,000 resources due to divestitures in 2014.
Cybersecurity
The company’s approach on cybersecurity leverages its ability
to adapt to a changing environment, as well as the depth and
breadth of its global capabilities, both in terms of its offerings
to clients and its internal approaches to risk management. The
company has commercial solutions that deliver identity and
access management, data security, application security, network
security and endpoint security. IBM’s solutions include a security
intelligence dashboard that can collect information on customer
IT security events and provide detailed information to custom-
ers about potential threats and security posture. The company’s
services businesses offer professional solutions for security from
assessment to deployment. In addition, the company offers man-
aged and outsourced security solutions from multiple security
operations centers around the world. Finally, security is embed-
ded in a multitude of IBM offerings through secure engineering
processes and by critical functions (encryption, access control,
etc.) in servers, storage, software, services and other solutions.
From an enterprise perspective, IBM implements a multi-
faceted risk-management approach to identify and address
cybersecurity risks. The company has established policies and
procedures that provide the foundation by which IBM’s infrastruc-
ture and data are managed. IBM performs ongoing assessments
regarding its technical controls and its methods for identifying
emerging risks related to cybersecurity. The company uses a
layered approach with overlapping controls to defend against
cybersecurity attacks on networks, end-user devices, datacen-
ters and applications. The company also has a global incident
response process to respond to cybersecurity threats. In addition,
the company utilizes a combination of online training, educational
tools, and other awareness initiatives to foster a culture of security
awareness and responsibility among its workforce.