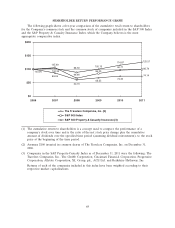
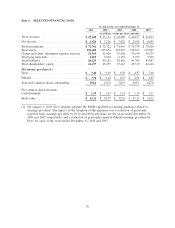
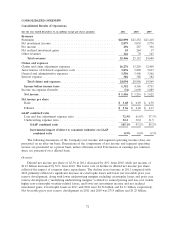
Travelers 2011 Annual Report Download - page 75
Download and view the complete annual report
Please find page 75 of the 2011 Travelers annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.The IAIS is also working with the Financial Stability Board created by the G-20 and is expected to
recommend a methodology for determining whether and which, if any, insurance companies pose a
systemic risk to the global economy. Such insurers would be designated ‘‘globally systemically important
financial institutions’’ (G-SIFIs) and would likely be subject to higher capital requirements, enhanced
supervision or both. The IAIS has not yet decided upon the criteria for or the consequences of such
designation.
Our business success and profitability depend, in part, on effective information technology systems
and on continuing to develop and implement improvements in technology. We depend in large part
on our technology systems for conducting business and processing claims, as well as for providing the
data and analytics we utilize to manage our business, and thus our business success is dependent on
maintaining the effectiveness of existing technology systems and on continuing to develop and enhance
technology systems that support our business processes and strategic initiatives in a cost and resource
efficient manner. Some system development projects are long-term in nature, may negatively impact
our expense ratios as we invest in the projects and may cost more than we expect to complete. In
addition, system development projects may not deliver the benefits we expect once they are complete,
or may be replaced or become obsolete more quickly than expected, which could result in accelerated
recognition of expenses. If we do not effectively and efficiently manage and upgrade our technology
portfolio, or if the costs of doing so are higher than we expect, our ability to provide competitive
services to new and existing customers in a cost effective manner and our ability to implement our
strategic initiatives could be adversely impacted.
If we experience difficulties with technology, data security and/or outsourcing relationships, our
ability to conduct our business could be negatively impacted. While technology can streamline many
business processes and ultimately reduce the cost of operations, technology initiatives present significant
risks. Our business is highly dependent upon our employees’ ability to perform, in an efficient and
uninterrupted fashion, necessary business functions. A shut-down of, or inability to access, one or more
of our facilities; a power outage; or a failure of one or more of our information technology,
telecommunications or other systems could significantly impair our ability to perform such functions on
a timely basis. In the event of a disaster such as a natural catastrophe, terrorist attack or industrial
accident, or due to a computer virus, our systems could be inaccessible for an extended period of time.
In addition, because our information technology and telecommunications systems increasingly interface
with and depend on third-party systems, we could experience service denials or failures of controls if
demand for our service exceeds capacity or a third-party system fails or experiences an interruption. If
our business continuity plans did not sufficiently address such a business interruption, system failure or
service denial, this could result in a deterioration of our ability to write and process new and renewal
business, provide customer service, pay claims in a timely manner or perform other necessary business
functions.
Our operations rely on the reliable and secure processing, storage and transmission of confidential
and other information in our computer systems and networks. Computer viruses, hackers, employee
misconduct and other external hazards could expose our data systems to security breaches, cyber
attacks or other disruptions. In addition, we routinely transmit and receive personal, confidential and
proprietary information by email and other electronic means. While we attempt to develop secure
transmission capabilities with third-party vendors and others with whom we do business, we may be
unable to put in place secure capabilities with all of such vendors and third parties and, in addition,
these third parties may not have appropriate controls in place to protect the confidentiality of the
information.
These increased risks, and expanding regulatory requirements regarding data security, could expose
us to data loss, disruption of service, monetary and reputational damages and significant increases in
compliance costs. As a result, our ability to conduct our business might be adversely affected.
63