Symantec 2015 Annual Report Download - page 3
Download and view the complete annual report
Please find page 3 of the 2015 Symantec annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
Dear Fellow Shareholders:
Cybersecurity continues to be the highest priority for consumers, enterprises,
and governments worldwide, and Symantec remains critical to meeting their
challenges. Nearly 317 million new pieces of malware were created in 2014, and no
organization is immune to these threats. In fact, hackers targeted five out of six large
companies with spear-phishing attacks in 2014, a 40% increase over the prior year.
During the same period, ransomware attacks increased 113%, threatening the
livelihoods of consumers and small businesses with costly interruptions – a threat
from which Symantec and Norton customers are protected. In addition, malware has
become increasingly sophisticated. For instance, up to 28% of all malware was
“virtual machine aware” in 2014, making it more challenging for security professionals to detect these
threats using traditional payload detonation techniques.
Several secular trends are accelerating innovation in the security market. The rapid shift to mobile
and cloud-based workloads has driven a resurgence in Symantec’s endpoint protection and data loss
prevention businesses even as they render perimeter security less relevant. The migration of enterprise
data and applications to the cloud, a scarcity of cybersecurity professionals, and increased government
and regulatory attention on cybersecurity are also creating significant market opportunities for Symantec.
We have one of the strongest security franchises in the world because we see more, analyze
more, and therefore defend against more cyber threats than any other company, protecting 175 million
endpoints, scanning 30% of the world’s enterprise email traffic per day, and deploying 57.6 million attack
sensors in 157 countries. With nearly 4 trillion rows of telemetry growing by 100 billion rows per month,
we operate the largest civilian threat database in the world. Our new security strategy, which we call
“Unified Security”, leverages this database to find and stop more threats before they affect our
customers. Many of our customers are telling us that they have never needed Symantec more.
With a strong market position at the nexus of these trends, we have the resources and expertise
to extend our lead in the cybersecurity industry. I could not be more excited about these opportunities
and am confident we have the right team in place to execute our strategy.
STRATEGIC AND OPERATIONAL FOCUS DROVE PROGRESS
We made critical progress in our multi-year transformation during fiscal year 2015. In May 2014,
we set five key priorities, including: 1-managing our businesses as a portfolio and optimizing certain
businesses for margin; 2-prioritizing investments for growth; 3-growing revenue and improving
efficiencies through eight initiatives; 4-attracting talent to our executive team; and 5-returning significant
cash to shareholders. In October 2014, we announced distinct strategies for our security and information
management businesses along with our decision to separate these businesses so each could be more
focused and flexible in the execution of those strategies.
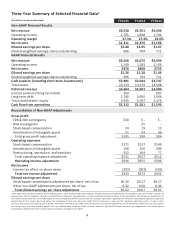
We improved our profitability by 50 basis points on a constant currency basis and delivered non-
GAAP1revenue of $6.5 billion. By managing our Norton segment for margin, we expanded its non-GAAP
operating margin from 45% in fiscal 2014 to 53% in fiscal 2015. We increased our non-GAAP R&D
spending by $89 million and shifted R&D dollars to focus on growth areas, delivering more than 50
enterprise security and information management products in fiscal 2015. We hired five new executives,
who bring valuable skills in analytics, backup and recovery software, sales, security, strategy, and human
1results are reconciled to GAAP on page 4
1