Symantec 2015 Annual Report Download - page 157
Download and view the complete annual report
Please find page 157 of the 2015 Symantec annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
losses from each of these cases. The final resolution of these lawsuits, individually or in the aggregate, is not
expected to have a material adverse effect on our business, results of operations, financial condition or cash flow.
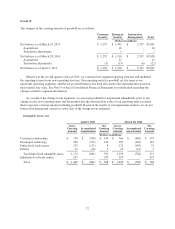
Note 8. Stock Repurchases
The following table summarizes our stock repurchases:
Year Ended
April 3, 2015 March 28, 2014 March 29, 2013
(In millions, except per share data)
Total number of shares repurchased 21 21 49
Dollar amount of shares repurchased $ 500 $ 500 $ 826
Average price paid per share $ 23.73 $ 23.87 $ 16.98
Remaining authorization at end of period $ 1,158 $ 658 $ 1,158
Through our stock repurchase programs we have repurchased shares on a quarterly basis since the fourth
quarter of fiscal 2004. On February 3, 2015, our Board of Directors authorized a new $1.0 billion stock
repurchase program which commenced immediately and does not have an expiration date. This is in addition to
the remaining amount authorized for future repurchase under our previous program.
Note 9. Segment and Geographic Information
In fiscal 2015, we are focused on managing our businesses as a portfolio and optimizing certain businesses
for margin or growth. As a result, in the second quarter of fiscal 2015 we formed a new consumer group and
modified our segment reporting structure to match our operating structure based on financial information
reviewed by our CODM. Consumer Security consists of our consumer businesses that were previously reported
in User Productivity & Protection. Enterprise Security consists of our enterprise security businesses that were
previously reported in User Productivity & Protection and Information Security. Our Information Management
segment was not impacted by the change in our operating structure. The three reporting segments, which are the
same as our operating segments, are as follows:
•Consumer Security: Our Consumer Security segment focuses on making it simple for customers to be
productive and protected at home and at work. Our Norton-branded services provide multi-layer
security and identity protection on major desktop and mobile operating systems, to defend against
increasingly complex online threats to individuals, families, and small businesses.
•Enterprise Security: Our Enterprise Security segment protects organizations so they can securely
conduct business while leveraging new platforms and data. These products include Secure Socket
Layer (“SSL”) Certificates, authentication, mail and web security, data center security, data loss
prevention, information security services, endpoint security and management, encryption, and mobile
security offerings.
•Information Management: Our Information Management segment focuses on backup and recovery,
archiving and eDiscovery, storage and high availability solutions, helping to ensure that our customers’
IT infrastructure and mission-critical applications are protected, managed and available.
79