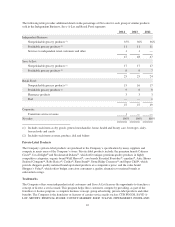
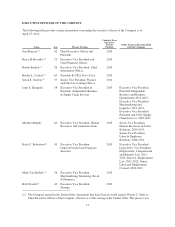
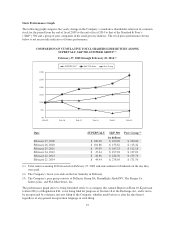
Albertsons 2014 Annual Report Download - page 22
Download and view the complete annual report
Please find page 22 of the 2014 Albertsons annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.breach by computer hackers and cyber terrorists. The Company relies on industry accepted security measures and
technology to securely maintain confidential and proprietary information maintained on the Company’s
information systems, and continues to invest in maintaining and upgrading the systems and applications to ensure
risk is controlled. However, these measures and technology may not adequately prevent security breaches. In
addition, the unavailability of the information systems or failure of these systems to perform as anticipated for
any reason, including any inability to access data stored in these systems, could disrupt the Company’s business
and could result in decreased performance and increased overhead costs, causing the Company’s business and
results of operations to suffer.
Additionally, the Company’s businesses involve the receipt and storage of sensitive data, including personal
information about the Company’s customers and employees and proprietary business information of the Company
and its customers and vendors. The Company may also share information with vendors that assist the Company in
conducting its business, as required by law, with the permission of the individual or as permitted under the
Company’s privacy policy. As a merchant that accepts debit and credit cards for payment, the Company is subject
to the Payment Card Industry Data Security Standard (“PCI DSS”), issued by the PCI Council. PCI DSS contains
compliance guidelines and standards with regard to the Company’s security surrounding the physical and electronic
storage, processing and transmission of individual cardholder data. By accepting debit cards for payment, the
Company is also subject to compliance with American National Standards Institute data encryption standards, and
payment network security operating guidelines. The Company currently complies with PCI DSS version 2.0;
however, the Company will be required to comply with the new PCI DSS version 3.0 by January 1, 2015.
Despite compliance with these standards and the utilization of other information security measures, the Company
cannot be certain that all of its IT systems or the IT systems of its vendors are or will be able to prevent, contain
or detect any cyber-attacks or security breaches from known malware, malware that may be developed in the
future or otherwise. Cyber-attacks are rapidly evolving and becoming increasingly sophisticated and difficult to
detect, and therefore, the Company may be unable to anticipate these attacks or implement adequate preventive
measures. Additionally, unauthorized parties may attempt to gain access to the Company’s or a vendor’s systems
or facilities through fraud, trickery or other forms of deception involving the Company’s employees or vendors.
To the extent that any attack or breach results in the loss, damage or misappropriation of information, the
Company may be adversely affected by claims from customers, financial institutions, payment card associations,
stockholders and others and by costly inquiries or enforcement actions on the part of regulatory authorities. The
Company’s operations could also be significantly disrupted by these claims, as well as by the need to spend
significant time and expense to fix or replace its systems. The Company could also lose credibility with its
customers and suffer damage to its reputation and future sales. In addition, the cost of complying with stricter
privacy and information security laws and standards, including PCI DSS version 3.0, and developing,
maintaining and upgrading technology systems to address future advances in technology, could be significant and
the Company could experience problems and interruptions associated with the implementation of new or
upgraded systems and technology or with maintenance or adequate support of existing systems.
Customers are increasingly using computers, tablets, mobile phones and other devices to shop in stores and
online and provide feedback and public commentary on their shopping experience, including prices.
Multichannel retailing is rapidly evolving. If the Company does not keep pace with changing customer
expectations and new developments and technology investments by its competitors, the Company’s ability to
compete and results of operations could be adversely affected. In addition, if the customer-facing technology
systems do not reliably function as designed, the Company may experience a loss of customer confidence or data
security breaches or be exposed to fraudulent purchases, which, if significant, could adversely affect the
Company’s reputation and results of operations.
The Company’s businesses are subject to laws and governmental regulations that could adversely impact
the Company’s financial condition and results of operations.
The Company’s businesses are subject to various federal, state and local laws, regulations and administrative
practices. These laws require the Company to comply with numerous provisions regulating health and sanitation
20