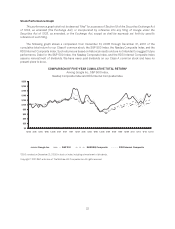
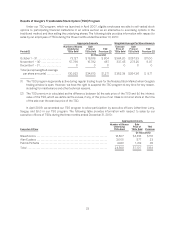
Google 2010 Annual Report Download - page 26
Download and view the complete annual report
Please find page 26 of the 2010 Google annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.liability. Our security measures may be breached due to the actions of outside parties, employee error,
malfeasance, or otherwise, and, as a result, an unauthorized party may obtain access to our data or our users’ or
customers’ data. Additionally, outside parties may attempt to fraudulently induce employees, users, or customers
to disclose sensitive information in order to gain access to our data or our users’ or customers’ data. Any such
breach or unauthorized access could result in significant legal and financial exposure, damage to our reputation,
and a loss of confidence in the security of our products and services that could potentially have an adverse effect
on our business. Because the techniques used to obtain unauthorized access, disable or degrade service, or
sabotage systems change frequently and often are not recognized until launched against a target, we may be
unable to anticipate these techniques or to implement adequate preventative measures. If an actual or perceived
breach of our security occurs, the market perception of the effectiveness of our security measures could be
harmed and we could lose users and customers.
We are, and may in the future be, subject to intellectual property or other claims, which are costly to
defend, could result in significant damage awards, and could limit our ability to use certain technologies
in the future.
Internet, technology, and media companies own large numbers of patents, copyrights, trademarks, and trade
secrets and frequently enter into litigation based on allegations of infringement or other violations of intellectual
property rights. In addition, patent holding companies may continue to seek to monetize patents they have
purchased or otherwise obtained. As we have grown, the intellectual property rights claims against us have
increased and may continue to increase as we develop new products, services, and technologies.
We have had patent, copyright, and trademark infringement lawsuits filed against us claiming that certain of
our products, services, and technologies, including Android, Google WebSearch, Google AdWords, Google
AdSense, Google News, Google Image Search, Google Chrome, Google Talk, Google Voice, and YouTube, infringe
the intellectual property rights of others. Adverse results in these lawsuits may include awards of substantial
monetary damages, costly royalty or licensing agreements, or orders preventing us from offering certain features,
functionalities, products, or services, and may also result in a change in our business practices, and require
development of non-infringing products or technologies, which could result in a loss of revenues for us and
otherwise harm our business.
In addition, many of our agreements with our customers and partners require us to indemnify them for certain
intellectual property infringement claims against them, which would increase our costs as a result of defending
such claims, and may require that we pay significant damages if there were an adverse ruling in any such claims.
Furthermore, such customers and partners may discontinue the use of our products, services, and technologies,
as a result of injunctions or otherwise, which could result in loss of revenues and adversely impact our business.
Regardless of the merits of the claims, intellectual property claims are often time-consuming, expensive to
litigate or settle, and cause significant diversion of management attention. To the extent such intellectual property
infringement claims are successful, they may have an adverse effect on our business, consolidated financial
position, results of operations, and cash flow.
Our intellectual property rights are valuable, and any inability to protect them could reduce the value
of our products, services, and brand.
Our patents, trademarks, trade secrets, copyrights, and other intellectual property rights are important assets
for us. Various events outside of our control pose a threat to our intellectual property rights, as well as to our
products, services and technologies. For example, effective intellectual property protection may not be available in
every country in which our products and services are distributed or made available through the internet. Also, the
efforts we have taken to protect our proprietary rights may not be sufficient or effective.
Although we seek to obtain patent protection for our innovations, it is possible we may not be able to protect
some of these innovations. Moreover, because of our long-term interests in open source, we may not have
13