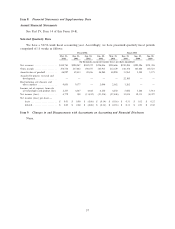
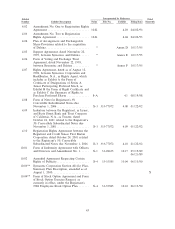
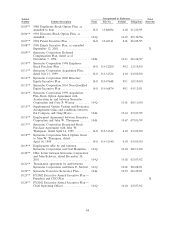
Symantec 2002 Annual Report Download - page 57
Download and view the complete annual report
Please find page 57 of the 2002 Symantec annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.We must attract and retain personnel in a competitive marketplace. We believe that our future success
will depend in part on our ability to recruit and retain highly skilled management, marketing and technical
personnel. To accomplish this, we believe that we must provide personnel with a competitive compensation
package, including stock options. Increases in shares available for issuance under our stock options plans
require stockholder approval in many cases, and institutional stockholders, or stockholders generally, may not
approve future increases. Additionally, there are several proposals in the Congress and in the accounting
industry to require corporations to include a compensation expense in their statement of operations relating to
the issuance of employee stock options. If such a measure is approved, we may decide to issue fewer stock
options. As a result, we may be impaired in our eÅorts to attract and retain necessary personnel.
Our intellectual property and proprietary rights may not be adequately protected from all unauthorized
uses. We regard our software and underlying technology as proprietary. We seek to protect our proprietary
rights through a combination of conÑdentiality agreements and copyright, patent, trademark and trade secret
laws. Third parties may copy aspects of our products or otherwise obtain and use our proprietary information
without authorization or develop similar technology independently. All of our products are protected by
copyright laws, and we have a number of patents and patent applications pending. We may not achieve the
desired protection from, and third parties may design around, our patents. In addition, existing copyright laws
aÅord limited practical protection. Furthermore, the laws of some foreign countries do not oÅer the same level
of protection of our proprietary rights as the laws of the United States, and we may be subject to unauthorized
use of our products. Any legal action that we may bring to protect proprietary information could be expensive
and may distract management from day-to-day operations.
Our products are complex and are operated in a wide variety of computer conÑgurations, which could
result in errors or product failures. Because we oÅer very complex products, undetected errors, failures or
bugs may occur when they are Ñrst introduced or when new versions are released. Our products often are
installed and used in large-scale computing environments with diÅerent operating systems, system manage-
ment software and equipment and networking conÑgurations, which may cause errors or failures in our
products or may expose undetected errors, failures or bugs in our products. In the past, we have discovered
software errors, failures and bugs in certain of our product oÅerings after their introduction and have
experienced delays or lost revenues during the period required to correct these errors. Our customers'
computer environments are often characterized by a wide variety of standard and non-standard conÑgurations
that make pre-release testing for programming or compatibility errors very diÇcult and time-consuming.
Despite testing by us and by others, errors, failures or bugs may not be found in new products or releases after
commencement of commercial shipments. Errors, failures or bugs in products released by us could result in
negative publicity, product returns, loss of or delay in market acceptance of our products or claims by
customers or others. In addition, if an actual or perceived breach of network security occurs in one of our end
customer's security systems, regardless of whether the breach is attributable to our products, the market
perception of the eÅectiveness of our products could be harmed. Because the techniques used by computer
hackers to access or sabotage networks change frequently and generally are not recognized until launched
against a target, we may be unable to anticipate these techniques. Alleviating any of these problems could
require signiÑcant expenditures of our capital and resources and could cause interruptions, delays or cessation
of our product licensing, which could cause us to lose existing or potential customers and would adversely
aÅect results of operations.
Most of our license agreements with customers contain provisions designed to limit our exposure to
potential product liability claims. It is possible, however, that these provisions may not prove eÅective in
limiting our liability.
Increased utilization and costs of our technical support services may adversely aÅect our Ñnancial results.
Like many companies in the software industry, technical support costs comprise a signiÑcant portion of our
operating costs and expenses. Over the short term, we may be unable to respond to Öuctuations in customer
demand for support services, including periods of high customer usage in which delays may be experienced.
We also may be unable to modify the format of our support services to compete with changes in support
services provided by competitors. Further, customer demand for these services could cause increases in the
costs of providing such services and adversely aÅect our operating results.
35