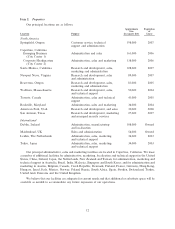
Symantec 2002 Annual Report Download - page 32
Download and view the complete annual report
Please find page 32 of the 2002 Symantec annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.business models and sectors fall out of our strategic requirements. We pursue investments, which we believe
will be complementary and which we believe can enhance both Ñnancial returns and market growth.
We use strategic acquisitions as necessary to provide certain technology, people and products for our
overall product strategy. We consider both timeliness to market and potential market share growth when
evaluating acquisitions of technologies, product lines or companies. We have completed a number of
acquisitions of technologies, companies and products, in the past, and have also disposed of technologies and
products. We may acquire and/or dispose of other technologies, companies and products in the future. For
further discussion on our acquisitions and divestitures, see Note 3 of Notes to Consolidated Financial
Statements of this Form 10-K.
Competition
Our markets are intensely competitive and are subject to rapid changes in technology. They are
inÖuenced by the rapid change in Internet security threats and the strategic direction of major computer
hardware manufacturers, Internet service providers, application service providers, key application software
vendors and operating system providers. Our competitiveness depends on our ability to deliver products that
meet our customers' needs by enhancing our existing solutions and oÅering reliable, scalable and standardized
new solutions on a timely basis. We have limited resources, and as a result, we must deploy our available
resources thoughtfully. The principal competitive factors in our Enterprise Security and Administration and
Consumer Products segments are quality, employment of the most advanced technology, time to market,
price, reputation, breadth of product oÅerings, customer support, brand recognition, and sales and marketing
teams. In our Services segment, the principal competitive factors include technical capability, customer
responsiveness, price, ability to attract and retain talented and experienced personnel, and reputation within
the industry.
In the enterprise security and administration market, we compete against several companies who oÅer
competing products to our technology solutions and to our Symantec Ghost and pcAnywhere products and
competing services to our response and support. Some of the companies that we compete against are Altiris,
BindView, Checkpoint, Cisco, Computer Associates, Internet Security Services, Netopia, NetScreen, Net-
work Associates, Okena, PentaSafe, PowerQuest, Stac Software, SonicWALL, Sophos, Traveling Software,
Trend Micro, Watchguard and WebSense. Some of the companies that oÅer competing products to our
Consumer Products oÅerings include Internet Security Services, McAfee.com, Network Associates, Norman,
OnTrack (now owned by Kroll), Panda, Trend Micro and ZoneLabs. With the recent outbreaks of viruses and
other Internet-based security threats, several other companies have entered the market and may become
signiÑcant competitors in the future.
Our Symantec Security Services competes with companies such as Counterpane, Internet Security
Services, Network Associates and Riptech.
Price competition is intense with most of our products and services. We expect price competition to
continue to increase and become even more signiÑcant in the future, which may reduce our proÑt margins.
We also face competition from a number of other products that oÅer levels of functionality diÅerent from
those oÅered by our products, or that were designed for a somewhat diÅerent group of end-users than those
targeted by us. Operating system vendors such as Microsoft have added security features to new versions of
their products that provide some of the same functions oÅered in our products. In addition, several other
operating systems are gaining market acceptance, such as Red Hat» Linux, Solaris and Unix-based operating
systems, and they may also incorporate some of the advanced utilities or other functionality oÅered in our
products. While we plan to continue to improve our products with a view toward providing enhanced
functionality over that provided in current and future operating systems, these eÅorts may be unsuccessful and
any improved products may not be commercially accepted by users. We will also continue to attempt to
cooperate with operating system vendors to make our products compatible with those operating systems, while
at the same time, diÅerentiating our utility products from features included in those operating systems. Our
eÅorts in this regard may be unsuccessful.
10