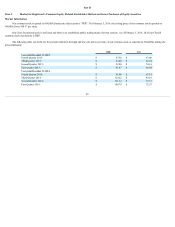
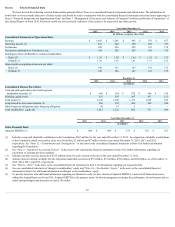
TripAdvisor 2015 Annual Report Download - page 23
Download and view the complete annual report
Please find page 23 of the 2015 TripAdvisor annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
eventscouldcausesysteminterruption,delaysandlossofcriticaldata,andcouldpreventusfromprovidingcontentandservicestousers,travelersand/orthird
partiesforasignificantperiodoftime.Ifweexperiencefrequentorpersistentsystemfailures,ourreputationandbrandcouldbepermanentlyandsignificantly
harmed.Inaddition,remediationmaybecostlyandwemaynothaveadequateinsurancetocoversuchcosts.Moreover,thecostsofenhancinginfrastructureto
attainimprovedstabilityandredundancymaybetimeconsumingandexpensiveandmayrequireresourcesandexpertisethataredifficulttoobtain.
Our processing, storage and use personal information and other data exposes us to risks of external and internal security breaches and could give rise to
liabilities.
Therearenumerouslawsregardingprivacyandthestoring,sharing,use,processing,disclosureandprotectionofpersonalinformationandotherconsumer
data,thescopeofwhicharechanging,subjecttodifferinginterpretations,andmaybeinconsistentbetweencountriesorconflictwithotherrules.Inaddition,the
securityofdatawhenengaginginelectroniccommerceisessentialtomaintainingconsumerandtravelserviceproviderconfidencesinourservices.Westriveto
complywithallapplicablelaws,policies,legalobligationsandindustrycodesofconductrelatingtoprivacyanddataprotection.Anyfailureorperceivedfailureby
ustocomplywithourprivacypolicies,privacy-relatedobligationstousersorotherthirdparties,orprivacy-relatedlegalobligations,oranycompromiseofsecurity
thatresultsintheunauthorizedreleaseortransferofpersonallyidentifiableinformationorotheruserdata,mayresultingovernmentalenforcementactions,
litigationorpublicstatementsthatcouldharmourreputationandcauseourcustomersandmemberstolosetrustinus,whichcouldhaveanadverseeffectonour
business,brand,marketshareandresultsofoperations.
Theregulatoryframeworkforprivacyissuesworldwideiscurrentlyinfluxandislikelytoremainsofortheforeseeablefuture.Practicesregardingthe
collection,use,storage,transmissionandsecurityofpersonalinformationbycompaniesoperatingovertheInternethaverecentlycomeunderincreasedpublic
scrutiny.TheU.S.Congressandfederalagencies,includingtheFederalTradeCommissionandtheDepartmentofCommerce,arereviewingtheneedforgreater
regulationforthecollectionanduseofinformationconcerningconsumerbehaviorontheInternet.VariousU.S.courtsarealsoconsideringtheapplicabilityof
existingfederalandstatestatutes,includingcomputertrespassandwiretappinglaws,tothecollectionandexchangeofinformationonline.Inaddition,the
EuropeanUnionisintheprocessofproposingreformstoitsexistingdataprotectionlegalframework,whichmayresultinagreatercomplianceburdenfor
companies,includingus,withusersinEuropeandincreasedcostsofcompliance.
Potentialsecuritybreachestooursystems,whetherresultingfrominternalorexternalsources,couldsignificantlyharmourbusiness.Aparty,whether
internalorexternal,thatisabletocircumventoursecuritysystemscouldmisappropriateuserinformationorproprietaryinformationorcausesignificant
interruptionsinouroperations.Inthepast,wehaveexperienced“denial-of-service”typeattacksonoursystemsthathavemadeportionsofourwebsites
unavailableforshortperiodsoftimeaswellasunauthorizedaccessofoursystemsanddata.Wehaveacquiredanumberofcompaniesovertheyearsandmay
continuetodosointhefuture.Whilewemakesignificanteffortstoaddressanyinformationtechnologysecurityissueswithrespecttoouracquisitions,wemay
stillinheritsuchriskswhenweintegratetheacquiredbusinesses.Wemayneedtoexpendsignificantresourcestoprotectagainstsecuritybreachesorto
investigateandaddressproblemscausedbybreaches,andreductionsinwebsiteavailabilitycouldcausealossofsubstantialbusinessvolumeduringtheoccurrence
ofanysuchincident.Becausethetechniquesusedtosabotagesecuritychangefrequently,oftenarenotrecognizeduntillaunchedagainstatargetandmayoriginate
fromlessregulatedandremoteareasaroundtheworld,wemaybeunabletoproactivelyaddressthesetechniquesortoimplementadequatepreventivemeasures.
Securitybreachescouldresultinnegativepublicity,damagetoreputation,exposuretoriskoflossorlitigationandpossibleliabilityduetoregulatorypenaltiesand
sanctions.Securitybreachescouldalsocausetravelersandpotentialuserstoloseconfidenceinoursecurity,whichwouldhaveanegativeeffectonthevalueofour
brand.Failuretoadequatelyprotectagainstattacksorintrusions,whetherforourownsystemsorsystemsofvendors,couldexposeustosecuritybreachesthat
couldhaveanadverseimpactonfinancialperformance.
WealsofacerisksassociatedwithsecuritybreachesaffectingthirdpartiesconductingbusinessovertheInternet.Muchofourbusinessisconductedwith
thirdpartymarketingaffiliatesor,morerecently,thoughbusinesspartnerspoweringourinstantbookingfeature.Inaddition,wefrequentlyusethirdpartiesto
processcreditcardpayments.Asecuritybreachatsuchthirdpartycouldbeperceivedbyconsumersasasecuritybreachofoursystemsandcouldresultin
negativepublicity,damageourreputation,exposeustoriskoflossorlitigationandpossibleliabilityandsubjectustoregulatorypenaltiesandsanctions.In
addition,suchthirdpartiesmaynotcomplywithapplicabledisclosurerequirements,whichcouldexposeustoliability.
We face increased risks as the level of our debt increases.
OnJune26,2015,weenteredintoanewcreditagreementwithrespecttoa$1billionfive-yearrevolvingcreditfacility.Thesearrangementsinclude
restrictivecovenantsthatmayimpactthewaywemanageourbusinessandmaylimitourabilitytosecuresignificantadditionalfinancinginthefutureonfavorable
terms.Ourabilitytosecureadditionalfinancingandsatisfyourfinancialobligationsunderindebtednessoutstandingfromtimetotimewilldependuponourfuture
operatingperformance,whichissubjecttothenprevailinggeneraleconomicandcreditmarketconditions,includinginterestratelevelsandtheavailabilityofcredit
generally,andfinancial,businessandotherfactors,manyofwhicharebeyondourcontrol.Inlightofperiodicuncertaintyinthecapitaland
20