Symantec 2003 Annual Report Download - page 8
Download and view the complete annual report
Please find page 8 of the 2003 Symantec annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
THE ENVIRONMENT OF RISK
The rapid adoption of technologies, including wireless networks,
broadband, and instant messaging, opens avenues for new
cyberthreats and new methods of attack. New vulnerabilities are
on the rise, and cybercriminals are faster and more innovative
than ever at exploiting them. The propagation of an attack has
accelerated from days and hours to minutes and seconds. By the
time users find out that a threat exists, they may have already
been hit. At the same time, these threats use ever more auto-
mated and effective methods to attack and propagate, so no single
defensive technology is adequate protection.
As more people interact online with their banks, retailers,
insurance companies, governments, schools, and health care
providers, the divide between individual users and the institution
or enterprise is increasingly blurred. Now institutions must extend
their security concerns to the systems their customers use to
connect with them. Governments around the world are recognizing
the sensitive nature of the growing amount of information avail-
able online, and are setting regulatory standards to protect it.
Many nations have already passed such regulations in the health
care and financial services industries.
Finally, as technology’s role in the global infrastructure con-
tinues to grow, so do the number of ways an attacker can exploit it.
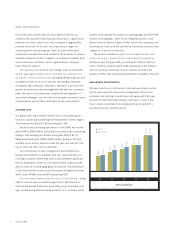
Within the last year, the number of new vulnerabilities, or “holes”
in software and hardware systems that allow unauthorized access
or the execution of malicious programs, grew more than 80%.
There’s no end in sight to the potential attacks or abuse of the
Internet and connected devices. But there is a way to protect
against the risks of an increasingly connected world—and realize
the opportunities technology has to offer.
TODAY, THE SAME CONNECTIVITY BREAKTHROUGHS THAT BRING NEW OPPORTUNITIES
TO PEOPLE AND BUSINESSES ALSO CREATE NEW RISKS.
6Symantec 2003