Symantec 2003 Annual Report Download - page 14
Download and view the complete annual report
Please find page 14 of the 2003 Symantec annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
12 Symantec 2003
WHAT WOULD THE FINANCIAL WORLD LOOK LIKE IF THERE WERE
NO CURRENCY?
What if your buying power were as close as your cell phone?
Before long, a WIRELESS CONNECTION to your bank
may be all you’ll need to purchase everything from a can of soda
to 100 shares of stock.
No cash. No coins. No checks or plastic.
No last-minute runs to the ATM. And while no technology can
eliminate bills, secure technology will make it possible
for bills to automatically “pay themselves” at your request—
through wireless transactions between banks and creditors.
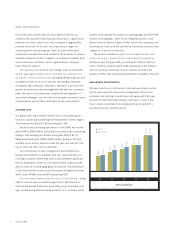
Security Comes From Inside—and Out
Because dozens of new threats and vulnerabilities are discovered every
day, security must be a dynamic process. It requires constant interaction
between the user and the partner they trust to provide around-the-clock
support against emerging threats and impending attacks. The solutions
deployed on a system or throughout a network are only as secure as the
last update. The security partner must have the infrastructure to support
its customers’ ongoing requirements for updates, information, and serv-
ice at all times—even under the pressure of a massive Internet attack.
Symantec provides timely, automatic updates of virus definitions,
intrusion detection signatures, firewall rules, filtering lists, vulnerability
signatures, and correlation engine rules to address emerging threats. Our
security research and response centers provide 24/7 global remediation
support from strategic locations around the world. Our security experts
in each center identify threats, analyze their impact, develop security
updates across Symantec’s broad range of solutions, and work with
customers, as needed, on personalized recovery strategies.
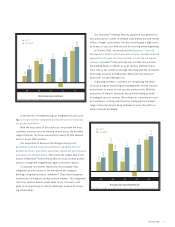
In addition, on an ongoing basis, Symantec conducts empirical
analyses of the more than 30 terabytes of data collected on network-
based attack activity, vulnerability discovery, and malicious code to offer
a reliable source of information about emerging trends in cybersecurity.
Our Internet Security Threat Report provides executives and IT adminis-
trators with benchmarks and guidance to help them evaluate the effec-
tiveness of their current and future security strategies.