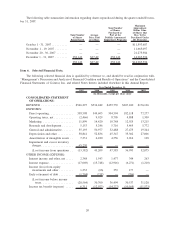
Redbox 2007 Annual Report Download - page 13
Download and view the complete annual report
Please find page 13 of the 2007 Redbox annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.In addition, we outsource to third-party providers certain aspects of our operating systems, including our long-
distance telecommunication network. Accordingly, the effectiveness of our operating systems is to a certain degree
dependent on the actions and decisions of our third-party providers.
Further, while we have taken significant steps to protect the security of our operating systems and have
established back-up systems and disaster recovery procedures, service disruptions may result from intentional or
unintentional acts of third parties, computer viruses, natural disasters, or other causes which are beyond our control.
Any service disruptions, whether due to errors or delays in or failure to adequately upgrade our software or
computing systems, interruptions or breaches in the communications network, inadequate back-up or disaster
recovery, or security breaches of the computer network system, caused by us or third parties, could seriously harm
our business, financial condition and results of operations.
Failure to adequately comply with information security policies or to safeguard against breaches of such pol-
icies could adversely affect our operations and could damage our business, reputation, financial position
and results of operations.
As our business expands to provide new products and services, including additional e-payment services, we are
increasing the amount of consumer data that we collect, transfer and retain as part of our business. These activities
are subject to laws and regulations, as well as industry standards, in the United States and other jurisdictions in
which our products and services are available. These requirements, which often differ materially and sometimes
conflict among the many jurisdictions in which we operate, are designed to protect the privacy of consumers’
personal information and to prevent that information from being inappropriately used or disclosed. We maintain and
review technical and operational safeguards designed to protect this information. However, despite those safe-
guards, it is possible that hackers, employees acting contrary to our policies, third-party agents or others could
improperly access our systems or improperly obtain or disclose data about our customers, or that we may be
determined not to be in compliance with applicable legal requirements and industry standards for data security, such
as the Payment Card Industry guidelines. Any breach of our security policies that compromises consumer data or
determination of non-compliance with applicable legal requirements or industry standards for data security could
expose us to regulatory enforcement actions, card association or other monetary fines or sanctions, or contractual
liabilities, limit our ability to provide our products and services, subject us to litigation and damage our reputation.
Lack of consumer confidence, whether real or perceived, in our coin-counting machines could harm our
business.
The accuracy of the coin-counting functionality of our machines is important to consumers and our retailers.
The failure to maintain consumer confidence in our technology and systems could harm our business. Our inability
to collect the data from our coin-counting machines could lead to a delay in processing coins and crediting the
accounts of our retailers for vouchers that have already been redeemed. Any inaccuracy, loss or delay in collecting
or processing coin data could seriously harm our operations.
Our future operating results may fluctuate.
Our future operating results will depend significantly on our ability to continue to drive new and repeat use of
our coin-counting, entertainment and e-payment products and services, our ability to develop and commercialize
new products and services and the costs incurred to do so, and our ability to successfully integrate new lines of
business into our operations, including, for example, money transfer services. Our operating results have a history of
fluctuating and may continue to fluctuate based upon many factors, including:
• the transaction fees we charge consumers to use our services
• the amount of service fees that we pay to our retailers,
• our ability to establish or maintain relationships with significant retailers on acceptable terms,
• the successful operation of our coin-counting, e-payment and DVD network,
11