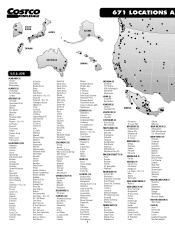
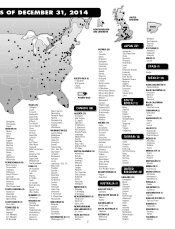
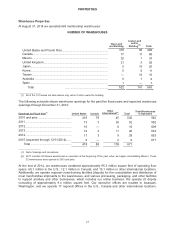
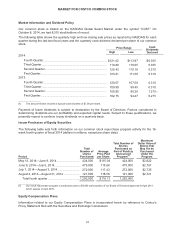
Costco 2014 Annual Report Download - page 17
Download and view the complete annual report
Please find page 17 of the 2014 Costco annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.telecommunications failures, computer viruses, internal or external security breaches, catastrophic events
such as fires, earthquakes, tornadoes and hurricanes, and errors by our employees. If our computer
systems or our back-up systems are damaged or cease to function properly, we may have to make
significant investments to fix or replace them, and we may suffer interruptions in our operations in the
interim. Any material interruption in our computer systems could have a material adverse effect on our
business and results of operations.
We are currently making, and will continue to make, significant technology investments to improve or
replace our information processes and systems that are key to managing our business. We must monitor
and choose the right investments and implement them at the right pace. The risk of system disruption is
increased when significant system changes are undertaken, although we believe that our change
management process can mitigate this risk. Excessive technological change could impact the
effectiveness of adoption, and could make it more difficult for us to realize benefits from the technology.
Targeting the wrong opportunities, failing to make the best investments, or making an investment
commitment significantly above or below our needs could result in the loss of our competitive position and
adversely impact our financial condition and results of operations. Additionally, the potential problems and
interruptions associated with implementing technology initiatives could disrupt or reduce the efficiency of
our operations in the short term. These initiatives might not provide the anticipated benefits or may
provide them on a delayed schedule or at a higher cost.
If we do not maintain the privacy and security of member-related and other business information,
we could damage our reputation with members, incur substantial additional costs, and become
subject to litigation.
We receive, retain, and transmit certain personal information about our members and entrust that
information to third party business associates, including cloud service providers who perform activities for
us. Our online business, which operates websites in the U.S., Canada, U.K., and Mexico, depends upon
the secure transmission of encrypted confidential information over public networks, including information
permitting cashless payments. A compromise of our security systems or those of our business associates
that results in our members' personal information being obtained by unauthorized persons could
adversely affect our reputation with our members and others, as well as our operations, results of
operations, financial condition and liquidity, and could result in litigation against us or the imposition of
penalties. In addition, a security breach could require that we expend significant additional resources
related to the security of information systems and could result in a disruption of our operations.
Additionally, the use of individually identifiable data by our business and our business associates is
regulated at the national and local or state level in all of our operating countries. Privacy and information
security laws and regulations change, and compliance with them may result in cost increases due to
necessary systems changes and the development of new administrative processes. If we, or those with
whom we share information, fail to comply with these laws and regulations or experience a data security
breach, our reputation could be damaged, possibly resulting in lost future business, and we could be
subjected to additional legal risk as a result of non-compliance.
Our security measures may be undermined due to the actions of outside parties, employee error,
malfeasance, or otherwise, and, as a result, an unauthorized party may obtain access to our data
systems and misappropriate business and personal information. Because the techniques used to obtain
unauthorized access, disable or degrade service, or sabotage systems change frequently and may not
immediately produce signs of intrusion, we may be unable to anticipate these techniques, timely discover
them, or implement adequate preventative measures. Any such breach or unauthorized access could
result in significant legal and financial exposure, damage to our reputation, and potentially have an
adverse effect on our business.
15