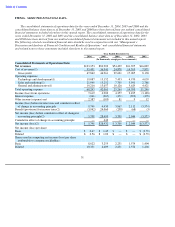
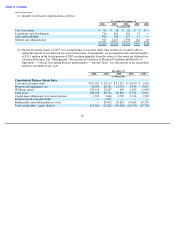
Shutterfly 2007 Annual Report Download - page 31
Download and view the complete annual report
Please find page 31 of the 2007 Shutterfly annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
Table of Contents
comply with applicable legislation, which claims may be expensive to defend and could divert management’s time
and attention. If we become subject to such claims in the future, or are required or elect to curtail or eliminate our use
of free offers, our results of operations may be harmed.
Our failure to protect the confidential information of our customers and networks against security breaches and
the risks associated with credit card fraud could damage our reputation and brand and substantially harm our
business and results of operations.
A significant prerequisite to online commerce and communications is the secure transmission of confidential
information over public networks. Our failure to prevent security breaches could damage our reputation and brand
and substantially harm our business and results of operations. For example, a majority of our sales are billed to our
customers’ credit card accounts directly, orders are shipped to a customer’s address, and customers log on using their
e-mail address. We rely on encryption and authentication technology licensed from third parties to effect the secure
transmission of confidential information, including credit card numbers. Advances in computer capabilities, new
discoveries in the field of cryptography or other developments may result in a compromise or breach of the
technology used by us to protect customer transaction data. In addition, any party who is able to illicitly obtain a
user’s password could access the user’s transaction data or personal information. Any compromise of our security
could damage our reputation and brand and expose us to a risk of loss or litigation and possible liability which would
substantially harm our business and results of operations. In addition, anyone who is able to circumvent our security
measures could misappropriate proprietary information or cause interruptions in our operations. We may need to
devote significant resources to protect against security breaches or to address problems caused by breaches.
In addition, under current credit card practices, we are liable for fraudulent credit card transactions because we
do not obtain a cardholder’s signature. We do not currently carry insurance against this risk. To date, we have
experienced minimal losses from credit card fraud, but we continue to face the risk of significant losses from this
type of fraud. Our failure to adequately control fraudulent credit card transactions could damage our reputation and
brand and substantially harm our business and results of operations.
Changes in regulations or user concerns regarding privacy and protection of user data could harm our
business.
Federal, state and international laws and regulations may govern the collection, use, sharing and security of data
that we receive from our customers. In addition, we have and post on our website our own privacy policies and
practices concerning the collection, use and disclosure of customer data. Any failure, or perceived failure, by us to
comply with our posted privacy policies or with any data-related consent orders, Federal Trade Commission
requirements or other federal, state or international privacy-related laws and regulations could result in proceedings
or actions against us by governmental entities or others, which could potentially harm our business. Further, failure
or perceived failure to comply with our policies or applicable requirements related to the collection, use or security of
personal information or other privacy-related matters could damage our reputation and result in a loss of customers.
Expansion of our international operations will require management attention and resources and may be
unsuccessful, which could harm our future business development and existing domestic operations.
To date, we have conducted limited international operations, but we intend to expand into international markets
in order to grow our business. These expansion plans will require management attention and resources and may be
unsuccessful. We have limited experience adapting our products to conform to local cultures, standards and policies.
We may have to compete with local companies which understand the local market better than we do. In addition, to
achieve satisfactory performance for consumers in international locations it may be necessary to locate physical
facilities, such as production facilities in the foreign market. We do not have experience establishing such facilities
overseas. We may not be successful in expanding into any international markets or in generating revenues from
foreign operations. In addition, different privacy, censorship and liability standards and regulations and different
intellectual property laws in foreign countries may cause our business to be harmed.
26