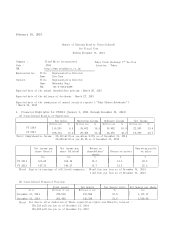
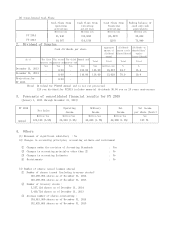
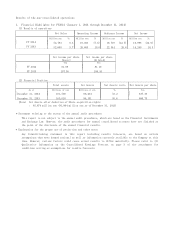
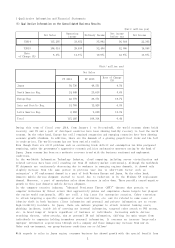
Trend Micro 2014 Annual Report Download - page 10
Download and view the complete annual report
Please find page 10 of the 2014 Trend Micro annual report below. You can navigate through the pages in the report by either clicking on the pages listed below, or by using the keyword search tool below to find specific information within the annual report.
fewer functions or were less effective in detecting and cleaning virus-infected files than our products and
services, customers could still choose these venders due to the lower cost.
In such a situation, our group’s business competitiveness could be inevitably weak, and it also has an
adverse effect on our business, financial condition, and results of operations.
THE POSSIBILITY OF DECRESED SALES AND MARKET SHARE IN OUR CORE JAPANESE MARKET IF OUR COMPETITORS ACHIEVE
SUCCESS IN JAPAN.
Our major competitors, McAfee, Inc. and Symantec Corporation, are active in the Japanese antivirus software
market and have allocated significant resources to achieve success in the Japanese computer security
market. Additionally, competition in our core Japanese market could intensify in the future if other
competitors emerge. As a result of our competitors’ efforts, we may not be able to maintain our current
leading market position in Japan in the future. Also, in order to respond effectively to increased
competition, we may be required to devote more of our product development, marketing and other resources to
the Japanese market, which could limit our ability to grow in other markets. A material loss of sales and
market share in Japan as a result of our competitors’ success could have a material adverse effect on our
business, financial condition and results of operations.
AS WE MAY ACQUIRE COMPANIES TO GROW OUR BUSINESS, FUTURE ACQUISITIONS MAY REDUCE OUR EARNINGS AND RESULT IN
INCREASED COSTS IN OUR BUSINESS OPERATIONS.
In a rapidly changing industry, we occasionally review acquisition opportunities. Accordingly, we may seek
to expand our business through acquisitions. Unlike some of our major competitors, we have limited
experience in acquiring existing businesses. Future acquisitions could result in numerous risks and
uncertainties, including:
•our inability to retain customers, suppliers and other important business relationships of an acquired
business;
•difficulties in integrating an acquired company into Trend Micro, including the acquired company’s
operations, personnel, products and information systems;
•diversion of our management’s attention from other business concerns; and
•adverse effects on our results of operations arising from acquisition-related charges, impairment of
goodwill and purchased technology and possible recognition of impairment charge.
If we make such an acquisition using our stock, our current shareholders’ ownership interests will be
diluted. Any of these factors could materially hurt our business, financial condition and results of
operations.
IF HACKERS / CRACKERS GAIN UNAUTHORIZED ACCESS TO OUR SYSTEMS, WE COULD SUFFER DISRUPTIONS IN OUR BUSINESS
AND LONG-TERM DAMAGE TO OUR REPUTATION.
Our reputation may be more susceptible to problems than other software companies caused by hackers /
crackers trying to break into or attack our networks, steal secrets, and deface our site. As a computer
security company that delivers virus protection and other security products and services over the Internet,
hackers / crackers specifically target us in order to cause us to transmit computer viruses and malware
programs, loss or theft of technical information including the source codes etc., or vital information of
customers or employees, and our groups’ website defacement over the internet. If these incidents occur,
our group’s business could suffer. We could also incur costs to fix technical problems or fix problems
created by hackers gaining access to our proprietary information. In addition, we could suffer substantial
disruptions in our business and damage to our reputation which could result in a significant loss of
customers and other important business relationships until recovery of confidence.
WE FACE INFORMATION SECURITY RISKS RELATED TO INSIDERS / OFFICIALS IN OUR GROUP.
Our group has made contracts with most of subcontractors and employees with the purpose of preservation of
confidentiality. In the case of loss or theft of technical or private information for taking out and unfair
use by our group insiders despite taking legislative actions, we could significantly discredit us.
Additionally, there is also a possibility to be brought an action for a large amount of damages. In such a
case, we could suffer substantial disruptions in our business and also incur costs to fix technical
problems etc. and any of these factors could materially hurt our business, financial condition and results
of operations.
WE FACE NEW RISKS RELATED TO OUR ANTI-VIRUS AND OTHER SECURITY PRODUCTS AND SERVICES.
A broad range of our security products may falsely identify emails, URLs, or programs as unwanted spam,
malicious web sites, and potentially dangerous programs. Our group’s security products and services may
also fail to properly identify and prevent unwanted emails, URLs, programs, malicious websites, or spyware
that are often designed to circumvent anti-virus, anti-spam, web filtering, or spyware products. Parties
7